The factors of digital authentication are organised into 3 categories and any number of these can be combined to create an increasingly secure authentication method:
- Knowledge. This is something that the user knows. The most common form of this factor is the username and password.
- Possession. This is something that the user owns. The most common form of this factor is the mobile phone.
- Inherence. This is something that is integral to the user themselves. The most common form of this factor is a user's fingerprints, voice, and retinas.
Successful technologies, such as the Internet, are incredibly desirable and useful and relatively affordable. Perhaps not all at first but they definitely build each other up in an endless cycle ultimately leading to huge growth.
As people's usage of the Internet's increases so does the amount of accounts that they create and, therefore, credentials that they have to remember. As the amount of credentials that they have to remember increases so does their carelessness.
As people's reliance on the Internet increases so does the amount of sensitive data that they upload. As the sensitivity of people's data grows so does the value of their data which draws the attention of thieves.
Sometimes, as a result, people's data is illegally obtained and even published via "hacks".
Some infamous but relatively isolated examples of this are the Apple iCloud 2014 celebrity photo hack where many celebrities had their extremely private and sensitive photos leaked to the public and the digital life dissolving of Wired's Mat Honan.
An infamous and very widespread example of this is the eBay hack of May 2014 where 145,000,000 - 233,000,000 eBay accounts were stolen, each including the person's name, encrypted password, email address, physical address, phone number, and date of birth.
For a much broader idea of how common and extensive these kind of events can be, though, refer to Beautiful's "World's Biggest Data Breaches" graph at http://www.informationisbeautiful.net/visualizations/worlds-biggest-data-breaches-hacks/.
These perpetrators are known as "black hat hackers" and they break into systems and steal data either for their own benefit or simply for the sake of anarchy. As Alfred once wisely said: "Well, because he thought it was good sport. Because some men aren't looking for anything logical, like money. They can't be bought, bullied, reasoned or negotiated with. Some men just want to watch the world burn."
There are many different attack vectors that hackers can use but generally they fall into the following categories:
- Social engineering. This is the psychological manipulation of people into performing actions or divulging confidential information.
- End user carelessness. This is when people are too lazy or ignorant to effectively manage their security.
- System exploits. This is when the system has a security flaw that can be discovered and exploited.
When it comes to the security of digital systems, the responsibility of security lies with both parties - the person should choose and maintain secure credentials for their account and the provider should securely transmit and store the account's credentials and data. However, these responsibilities aren't always taken as seriously as they should be.
I digress.
We are not security architects and if we choose to use a system then we can only protect our data as best as the tools provide.
You may be thinking that the obvious way to combat these threats is to increase the security of the factor by ensuring that people always choose unique and sufficiently-secure information. A good idea and one that a lot of systems now reinforce by, for example, displaying password strength meters (although, they should not be relied on for various reasons), not allowing a password to be set back to the same one, not allowing a password to reference other information, allowing people to create their own security questions, etc. However, as as much as they do try, this is simply not feasible because individual systems have no way to verify whether you're re-using credentials unless they're in communication with each other but that's an even bigger security risk.
So, what do we do? Well, a much better solution is not to increase the security of a single factor but to implement more factors - Multi Factor Authentication. This is commonly known as Two Factor Authentication and generally presents in the form of a Knowledge and Possession factor - a username and password plus a One Time Password obtained via an automated SMS or generated by an app. This is a very good system because it's a huge boost to security and still relatively convenient.
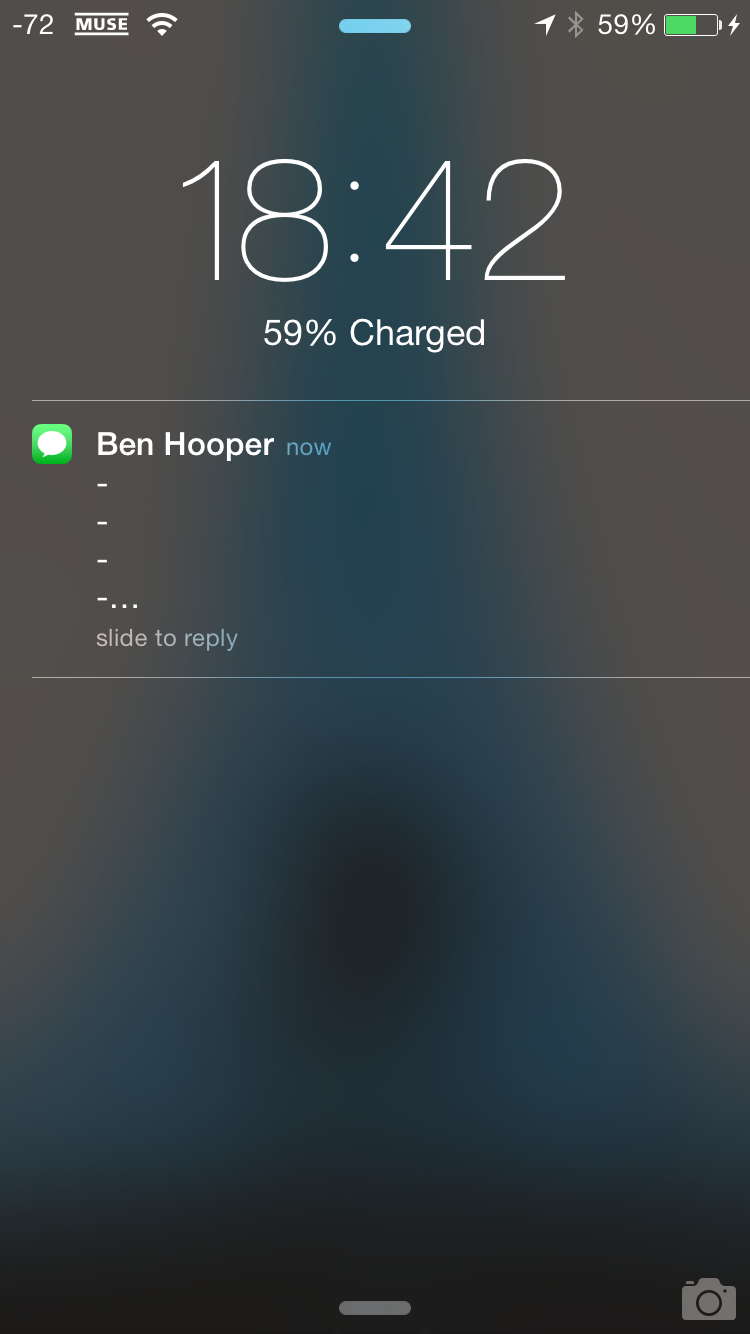
My only personal gripe with these systems is the way that the SMS codes are formatted. I can only speak for iOS but by default Settings > Notifications > Messages > Show Previews is enabled. This means that, although you do have to be in physical proximity to the device, you can simply read the SMS TFA code off the lock screen, like so:
It would not be hard to simply pad the code offscreen to avoid a security breach that is likely default on 1,000,000,000 iOS devices like so:
Oh, well. You can't have everything!
Disclaimer: I am not a security expert.